Authentication
From Business Process Management, BPM and Workflow Automation Wiki | BizAgi BPMS
<keywords content="keywords"> windows authentication, authentication, Bizagi authentication, password options, password, quick login, IIS authentication </keywords>
Contents |
Authentication
The security module includes an Authentication component that has great versatility in user management and validation. As soon as a user is created from the web application, the Bizagi Authentication is turned on by deafult.
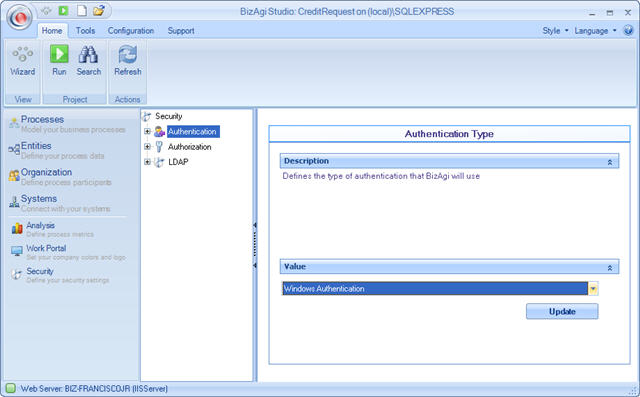
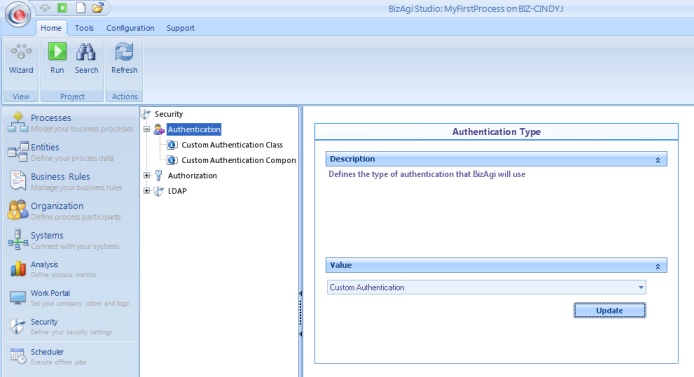
To configure authentication, identify the Security component in the Bizagi menu and click on the Authentication element; a new window will display in the work area the types of authentication available. Select the one desired and then click on the Update button.
These are several types of authentication for the Web Application. For more information about the configuration please click on How to Configure the Authentication.
|
Note: Authentication configuration will be taken to production in the first deployment. Henceforth, environments have independent configurations. |
Windows authentication
This type of authentication allows Bizagi to validate the users against domains and Windows machines automatically, provided the user is registered in Bizagi.
This module has no configuration option, which makes it very easy to use. The only thing to consider is that the user has to be created in the user administration module of Bizagi and as a user of the Windows domain.
According to the authentication methods of the web application, you may choose to present or not Bizagi's login page in the work portal.
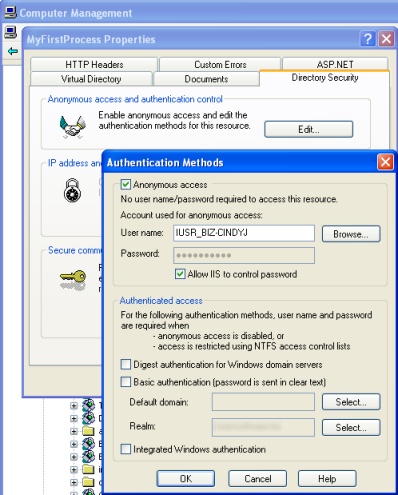
By default, the IIS site's configuration for a Bizagi work portal will show the login page (the users need to input the username, password and domain).
In order to not show the login page in Windows Authentication, anonymous access needs to be unmarked in the IIS site's configuration so that Bizagi can take the credentials from the Windows session.
View how to configure this type of authentication in Bizagi.
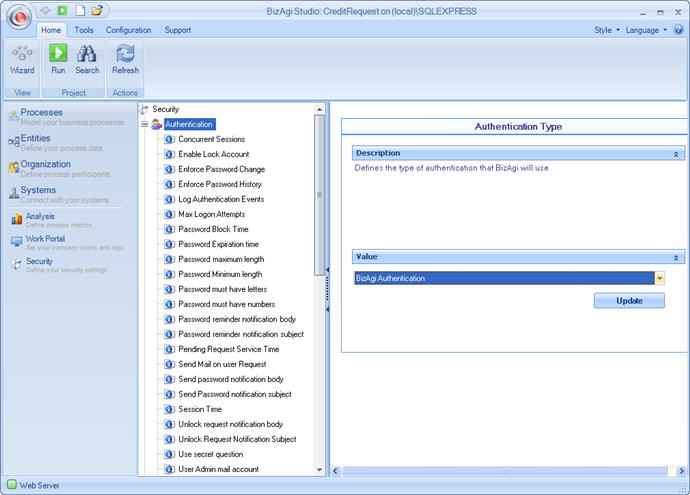
Bizagi authentication
By using this option, you are telling Bizagi that it has to handle authentication itself.
In order to do so, the users must be created by the administration module, as usual, and the password assigned must be entered in the “Password” field.
In addition, certain options that appear as sub-elements of the Authentication element must be configured once this type of authentication has been chosen.
Bizagi authentication has the following configuration options:
Options
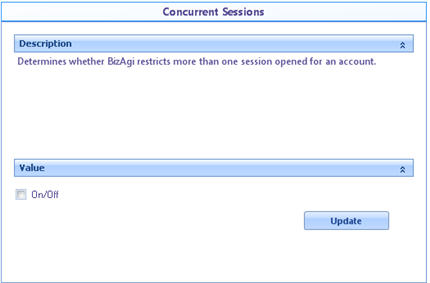
![]() Concurrent Sessions: If enabled it restricts the number of sessions opened for one account.
Concurrent Sessions: If enabled it restricts the number of sessions opened for one account.
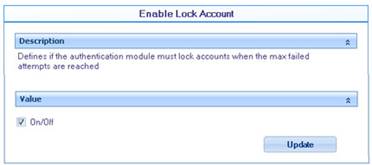
![]() Enable lock account: Enabled or disabled if the authentication module must lock accounts when the user reaches a specific number of attempts.
Enable lock account: Enabled or disabled if the authentication module must lock accounts when the user reaches a specific number of attempts.
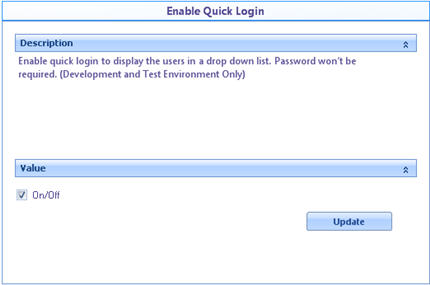
![]() Enable Quick Login: When enabled displays users created in a drop down list. To login password won't be necessary.
Enable Quick Login: When enabled displays users created in a drop down list. To login password won't be necessary.
This menu supports 100 users. From the 101th user there will be a text field availabe to type the name.
![]() Enforce password change: password must be changed after the first login
Enforce password change: password must be changed after the first login
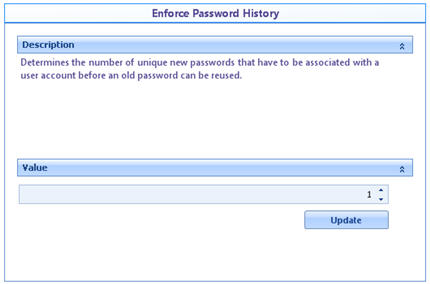
![]() Enforce password history: Number of unique passwords an account must have before using an old one.
Enforce password history: Number of unique passwords an account must have before using an old one.
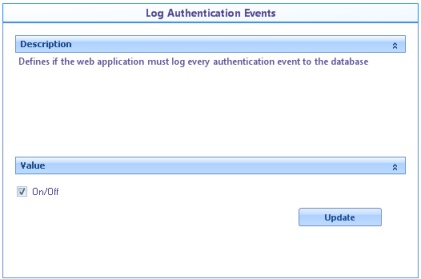
![]() Log authentication events: Indicates whether or not the web application must create an audit log of all authentication events.
Log authentication events: Indicates whether or not the web application must create an audit log of all authentication events.
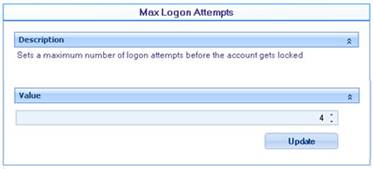
![]() Max logon attempts: Establishes a maximum number of attempts before the account is locked.
Max logon attempts: Establishes a maximum number of attempts before the account is locked.
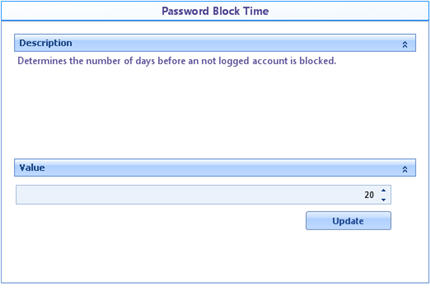
![]() Password block time: Number of days before a not logged on account is locked.
Password block time: Number of days before a not logged on account is locked.
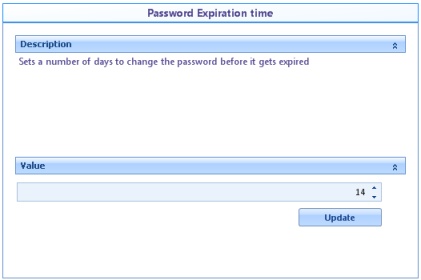
![]() Password expiration time: Establishes the maximum number of days for the account password to expire.
Password expiration time: Establishes the maximum number of days for the account password to expire.
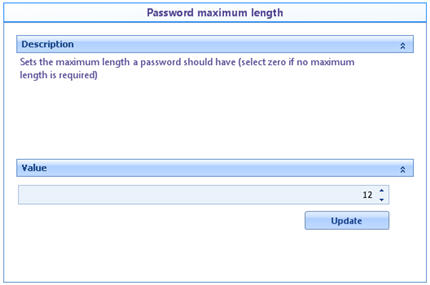
![]() Password maximum length: Defines the maximum number of characters for the password to be valid (zero if a maximum length is not required).
Password maximum length: Defines the maximum number of characters for the password to be valid (zero if a maximum length is not required).
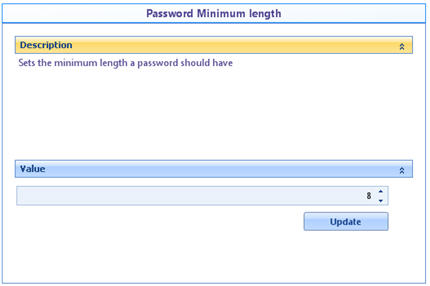
![]() Password minimum length: Defines the minimum number of characters for the password to be valid.
Password minimum length: Defines the minimum number of characters for the password to be valid.
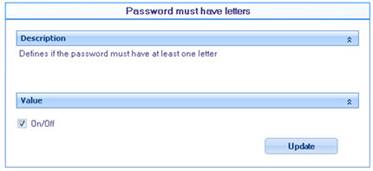
![]() Password must have letters: Defines whether or not to validate for the password to have at least one letter to be valid.
Password must have letters: Defines whether or not to validate for the password to have at least one letter to be valid.
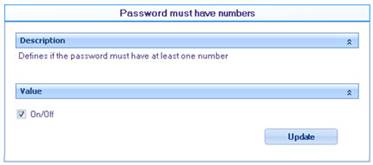
![]() Password must have numbers: Define whether or not to validate for the password to have at least one number to be valid.
Password must have numbers: Define whether or not to validate for the password to have at least one number to be valid.
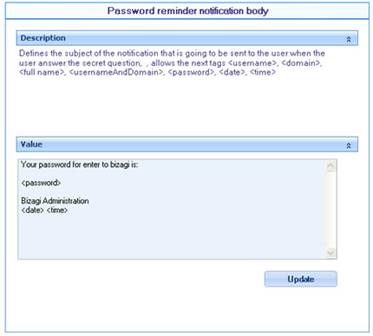
![]() Password reminder notification body: Defines the body of the mail to be sent when the user requests password reminder.
Password reminder notification body: Defines the body of the mail to be sent when the user requests password reminder.
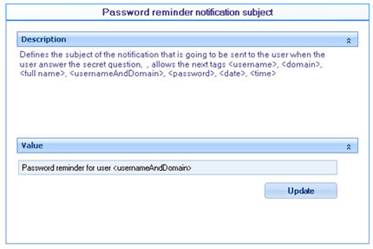
![]() Password reminder notification subject: Defines the subject of the mail to be sent when the user requests password reminder.
Password reminder notification subject: Defines the subject of the mail to be sent when the user requests password reminder.
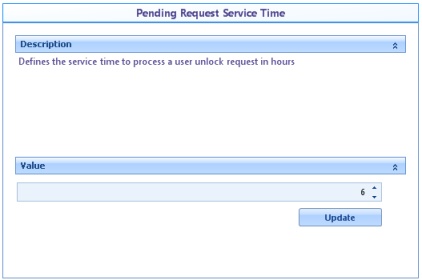
![]() Pending request service time: Defines the service time to process a pending request to unlock an account.
Pending request service time: Defines the service time to process a pending request to unlock an account.
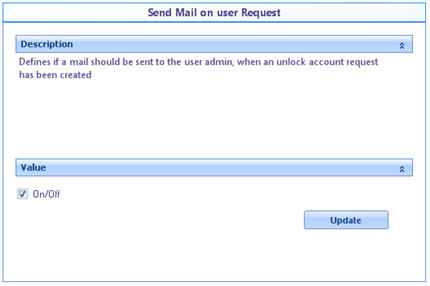
![]() Send Mail on user Request: Determines whether or not to send a notification when a user requests the unlocking of an account
Send Mail on user Request: Determines whether or not to send a notification when a user requests the unlocking of an account
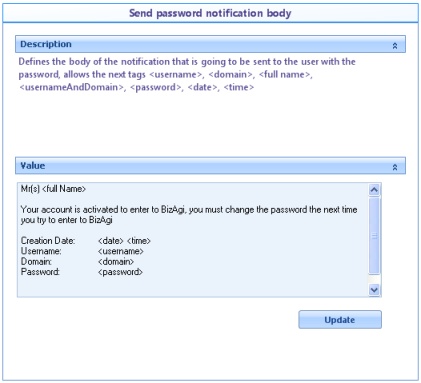
![]() Send password notification body: Defines the body of the mail to be sent when a user account is created and the password is sent to the user.
Send password notification body: Defines the body of the mail to be sent when a user account is created and the password is sent to the user.
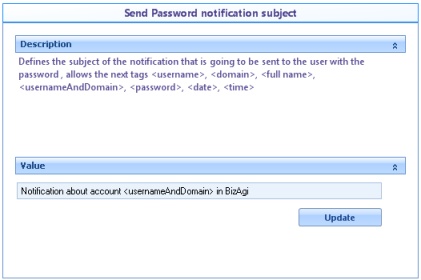
![]() Send password notification subject: Defines the subject of the mail to be sent when a mail account is created and the password is sent to the user.
Send password notification subject: Defines the subject of the mail to be sent when a mail account is created and the password is sent to the user.
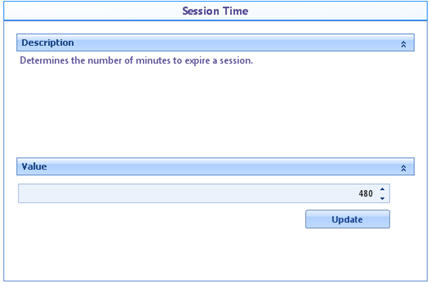
![]() Session time: Number of minutes to expire a session.
Session time: Number of minutes to expire a session.
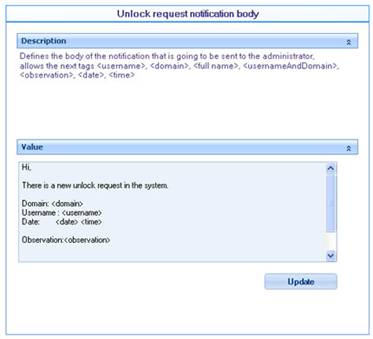
![]() Unlock Request Notification Body: Defines the body of the mail to be sent to the administrator when a user requests the unlocking of an account.
Unlock Request Notification Body: Defines the body of the mail to be sent to the administrator when a user requests the unlocking of an account.
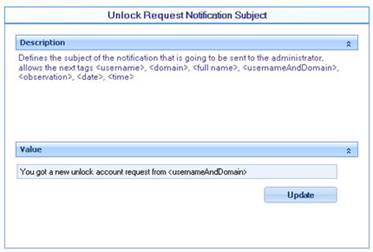
![]() Unlock Request Notification Subject: Defines the subject of the mail to be sent to the administrator when a user requests the unlocking of an account.
Unlock Request Notification Subject: Defines the subject of the mail to be sent to the administrator when a user requests the unlocking of an account.
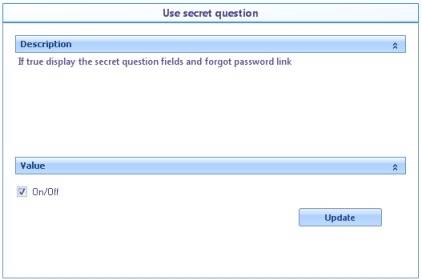
![]() Use secret question: If this option is enabled, the secret question and answer fields can be viewed.
Use secret question: If this option is enabled, the secret question and answer fields can be viewed.
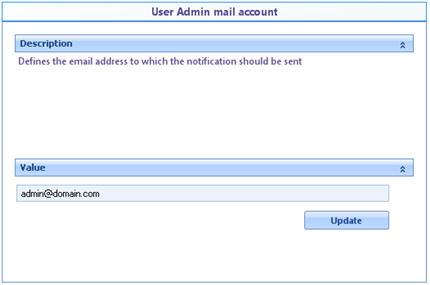
![]() User Admin Mail Account: Defines the e-mail used to send automatic notifications. This is also the e-mail where the administrator will be notify of the unlock account requests.
User Admin Mail Account: Defines the e-mail used to send automatic notifications. This is also the e-mail where the administrator will be notify of the unlock account requests.
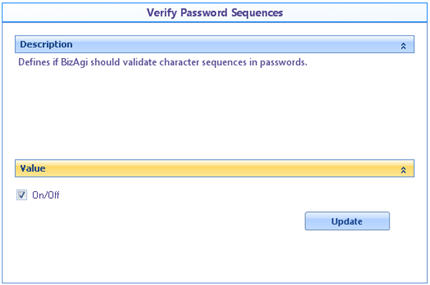
![]() Verify password Sequences : If enables Bizagi validates sequences in password.
Verify password Sequences : If enables Bizagi validates sequences in password.
LDAP authentication
For this type of authentication the information entered in the login page (username, password and domain) is sent to an LDAP server for verification.
The following options must be configured:
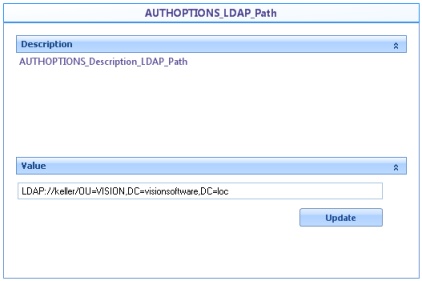
![]() AUTHOPTIONS_LDAP_Path: Corresponds to the path to access the LDAP server using the LDAP URL format.
AUTHOPTIONS_LDAP_Path: Corresponds to the path to access the LDAP server using the LDAP URL format.
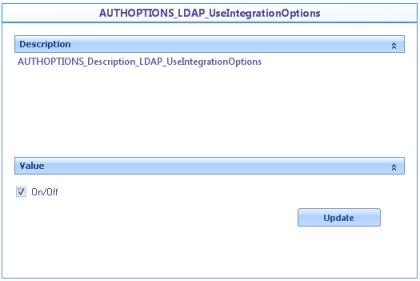
![]() AUTHOPTIONS_LDAP_UseIntegration: When Bizagi has been previously configured to include Active Directory users, turn on this option to use the same LDAP path. If it is checked, the value of the former option will be ignored.
AUTHOPTIONS_LDAP_UseIntegration: When Bizagi has been previously configured to include Active Directory users, turn on this option to use the same LDAP path. If it is checked, the value of the former option will be ignored.
It is necessary that the web application has only the Anonymous access selected as authentication method in the IIS for it to work correctly..
Mixed authentication
With this type of authentication, it is possible to configure 2 different types of authentications for users from different domains. One of the types must be Bizagi Authentication and the other may be either Windows or Custom Authentication (Custom authentication applies to the Enterprise .Net edition).
For example, if a Bizagi application is being accessed from the Internet as well as the intranet, configure Bizagi Authentication for users who access from the Internet, and Windows Authentication for users who access through the intranet.
When this type of authentication is chosen, configure the following options:
![]() Bizagi Authentication: as explained above.
Bizagi Authentication: as explained above.
![]() Windows Authentication/Custom Authentication: according to the selected value in Other Authentication Type, it would include same options as Custom Authentication or nothing, if Windows Authentication is selected.
Windows Authentication/Custom Authentication: according to the selected value in Other Authentication Type, it would include same options as Custom Authentication or nothing, if Windows Authentication is selected.
![]() Bizagi Domain: Name of the domain of the users who will be authenticated using Bizagi Authentication.
Bizagi Domain: Name of the domain of the users who will be authenticated using Bizagi Authentication.
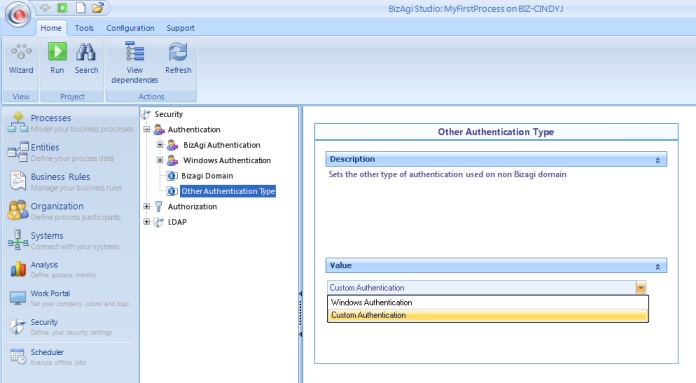
![]() Other Authentication Type: Select which other type of authentication (Windows or Custom) will be used. Remember that Custom authentication applies to the ENTERPRISE .NET EDITION.
Other Authentication Type: Select which other type of authentication (Windows or Custom) will be used. Remember that Custom authentication applies to the ENTERPRISE .NET EDITION.
Custom authentication (Applies to ENTERPRISE .NET EDITION and ENTERPRISE JEE EDITION)
|
Note: Custom authentication for the JEE edition is configured in the Application Server, by including additional settings in the JAAS module. |
When this option is selected, Bizagi is informed that the authentication will be handled by an external application, developed by a third party. If the data entered by the user and sent to the application returns True, Bizagi will grant access. If it returns False, access will be denied.
Custom authentication has the following configuration options:
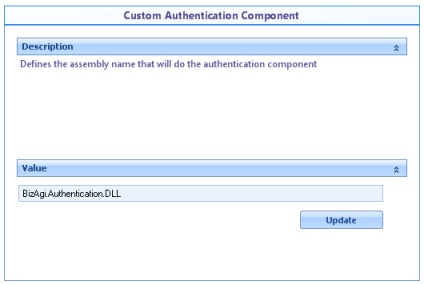
![]() Custom Authentication Component: Defines the name of the assembly that will perform the authentication. This assembly must be present in the application bin or in the GAC.
Custom Authentication Component: Defines the name of the assembly that will perform the authentication. This assembly must be present in the application bin or in the GAC.
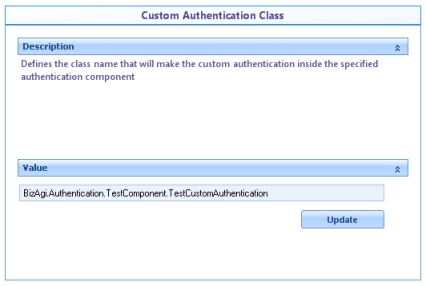
![]() Custom Authentication Class: Defines the name of the class that will perform the custom authentication within the component specified.
Custom Authentication Class: Defines the name of the class that will perform the custom authentication within the component specified.
Custom authentication Component
When Custom Authentication is activated, a component that contains a class that complies with a virtual contract must be created (it has to have certain given methods with specific parameters, but no interface to reduce mapping)
The authentication class must have the following function prototypes:
![]() public bool authenticate(string sDomain, string sUsername, string sPassword, ref string sErrorMessage)
public bool authenticate(string sDomain, string sUsername, string sPassword, ref string sErrorMessage)
This method is used to authenticate the user in the system. The domain, user and password are sent and a Boolean value is returned indicating successful authentication or not. In the latter case the sErrorMessage parameter must be filled with the corresponding error.
![]() public void logOff(string sDomain, string sUsername)
public void logOff(string sDomain, string sUsername)
This method is used to send the remote system a notification that the user left the system, or his/her session has been inactive.
![]() public bool changePassword(string sDomain, string sUsername, string sOldPassword, string sNewPassword, ref string sErrorMessage)
public bool changePassword(string sDomain, string sUsername, string sOldPassword, string sNewPassword, ref string sErrorMessage)
![]() public bool changePassword(string sDomain, string sUsername, string sOldPassword, string sNewPassword, string sSecretQuestion, string sSecretAnswer, ref string sErrorMessage)
public bool changePassword(string sDomain, string sUsername, string sOldPassword, string sNewPassword, string sSecretQuestion, string sSecretAnswer, ref string sErrorMessage)
These two methods are used to send the remote system a request for a password change. The second method contains an overload whereby the data of a secret question and answer are attached.
Integrated with Oracle Single-Sign-On (Applies to ENTERPRISE .NET EDITION)
To be used when an integration with Oracle Portal already exists. The same credentials entered by the user in the Oracle Portal will be used by Bizagi.
Configure the following options:
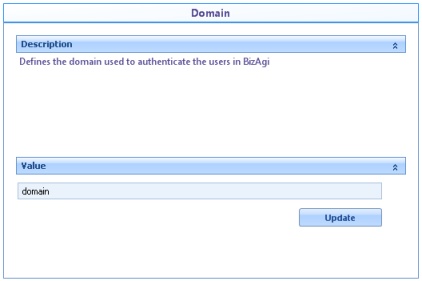
![]() Domain: Domain to be used for the authentication.
Domain: Domain to be used for the authentication.
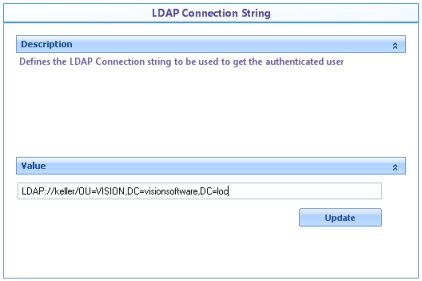
![]() LDAP Connection String: Corresponds to the path to access the LDAP server using the LDAP URL format.
LDAP Connection String: Corresponds to the path to access the LDAP server using the LDAP URL format.
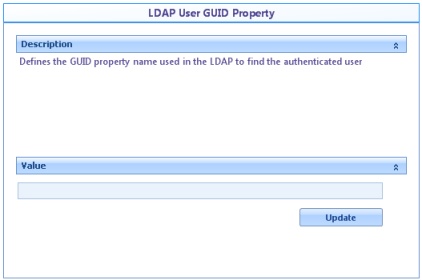
![]() LDAP User GUID Property: Enter the name of the GUID property, if it exists.
LDAP User GUID Property: Enter the name of the GUID property, if it exists.
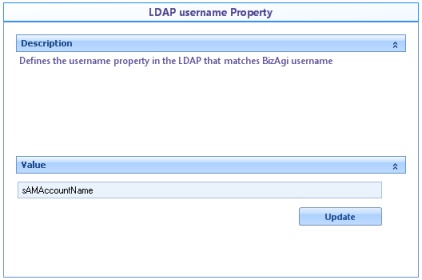
![]() LDAP username Property: Defines which property in LDAP matches Bizagi username.
LDAP username Property: Defines which property in LDAP matches Bizagi username.
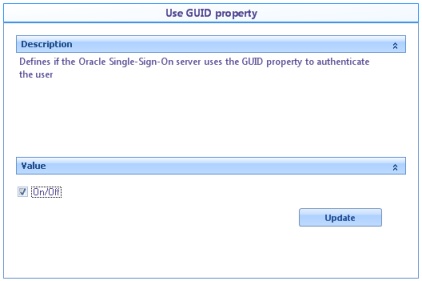
![]() Use GUID property: Enable this option if the GUID property is used to authenticate.
Use GUID property: Enable this option if the GUID property is used to authenticate.
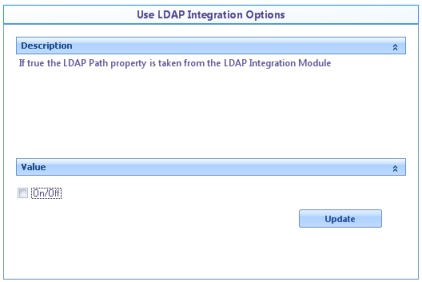
![]() Use LDAP Integration Options: When Bizagi has been previously configured to include Active Directory users, turn on this option so that the same LDAP path is used. If it is checked, the value of the LDAP Connection String option will be ignored.
Use LDAP Integration Options: When Bizagi has been previously configured to include Active Directory users, turn on this option so that the same LDAP path is used. If it is checked, the value of the LDAP Connection String option will be ignored.